A New Paradigm for Techno-Political Autonomy in 21st century
Part 1: How can we balance strategic autonomy in technological sovereignty with collaborative innovation?
Today, let’s explore a transformative idea: Open Specifications and JAM as the New Sovereignty of Technology.
To put things in perspective, let’s look back in time. In 1648, the Peace of Westphalia not only ended Europe’s Thirty Years’ War but also introduced a groundbreaking principle - national sovereignty. For the first time, the notion that each state holds the highest authority over its own territory, free from external interference, became a foundation of modern international relations.
This concept became a cornerstone of international relations. But now, nearly 400 years later, digital technologies are reshaping the global order yet again, creating a new paradigm: digital sovereignty.
Historically, national sovereignty has been defined by physical borders. But in this digital era, the rise of “virtual frontiers” is redefining how countries engage, govern, and assert influence. Digital sovereignty is the natural extension of national sovereignty into cyberspace, and it rests on three essential pillars:
1. Technology Sovereignty
2. Data Sovereignty
3. Digital Rule-making Sovereignty
Of these, technological sovereignty is foundational. Because in the digital age, sovereignty is not just about laws and land - it’s about whether a nation possesses the technological capacity to exercise power in cyberspace.
Yet, here’s the challenge: while national sovereignty may be equal in theory, digital sovereignty is anything but. Huge disparities in data resources and digital infrastructure have created deep asymmetries in wealth, influence, and security. A global Digital Dilemma is emerging.
As digital control becomes a new instrument of national security, power struggles are no longer about tanks or oil - they are about chips, clouds, and code. A complex triangle of interests - states, tech giants, and global rivals - is driving increasing tension and imbalance in the digital realm.
According to World-Systems Theory, global economies are divided into core, semi-periphery, and periphery nations. Today, the same hierarchy is emerging in digital terms:
- Digital Superpowers
- Emerging Digital Nations
- Digital Periphery Nations
Economist Robert Wade labels this structure as a system of digital dependence, where monopolies on key technologies force peripheral countries to rely on external infrastructure, undermining their sovereignty.
In a world of rising geopolitical uncertainty, this technological interdependence becomes dangerous. Politicized technologies can turn into weapons, while self-reliance risks isolation. Consider the facts:
- 99% of smartphones run on ARM architecture;
- The SWIFT network processes over $5 trillion daily;
- Global cloud infrastructure is dominated by U.S. and Chinese companies.
The dream of full technological autonomy feels increasingly out of reach. So what now?
The path forward is not isolation - but collaboration.
The United Nations’ “Global Digital Compact” (2024) reflects this reality: multilateral cooperation is the only viable response to global digital challenges.
As one of many countries grappling with the Digital Dilemma, China has proposed a unique approach - Collaborative Sovereignty, centered on an “independent and controllable nationalization” pathway. This model balances internal control with external engagement.
Building a networked community of shared destiny has become the fundamental basis of China’s “Collaborative Sovereignty” theory, offering a new approach to transforming the concept of national sovereignty and reshaping the order in the digital age.
In essence, “Collaborative Sovereignty” advocates for actively promoting global cooperation while steadfastly maintaining core technological autonomy. The new frontier of digital sovereignty calls for wisdom and responsibility. So, what is the key to breaking the deadlock in collaborative sovereignty?
The key lies in clarifying two core challenges of digital sovereignty:
-
First, how to construct resilient digital infrastructure that is both autonomous and globally interconnected?
-
Second, how to establish an internationally recognized global interoperability framework that balances strategic autonomy with collaborative innovation?
The answer lies deep in the logic of infrastructure.
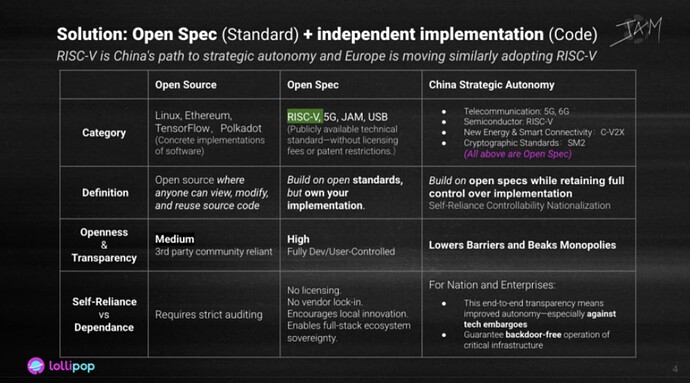
We’ve heard much about open-source software - transparent, modifiable, and community-driven. But today, we shift our focus to something even more foundational: Open Specifications.
Unlike open-source code, open specs define the rules - the shared standards that anyone can build on, without licensing fees or patent restrictions. Think of RISC-V: an open Instruction Set Architecture (ISA), not a piece of software. Anyone can design their own RISC-V-based chip without paying Intel or ARM millions of dollars in royalties.
This is why China chose RISC-V, 5G, SM2 encryption, and C-V2X as foundational to its tech sovereignty strategy. Open Spec + Independent Implementation ensures resilience, autonomy, and transparency, crucial in avoiding embargoes or vendor lock-in.
The benefits are compelling:
- No licensing traps
- No vendor dependencies
- Encouragement of local innovation
- Sovereignty across the entire technology stack
Europe is on the same path. RISC-V has become a strategic lever for reducing reliance on foreign chip tech and advancing digital independence.
Because here’s the shared insight:
Whoever defines the open specs, shapes the digital future.
Part 2: Why Nations Are Turning to JAM
Heading
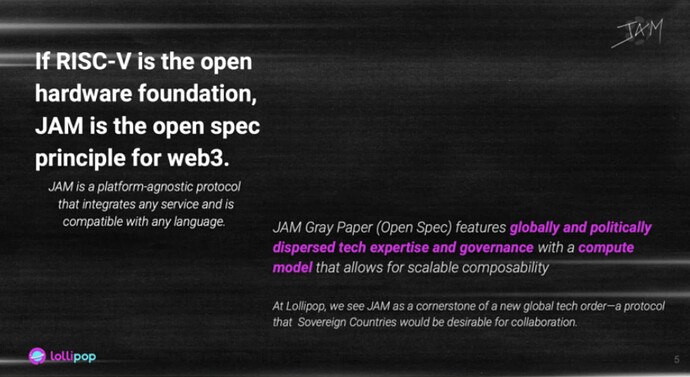
If RISC-V is the open spec foundation for hardware, then JAM is emerging as the open specification standard for Web3.
RISC-V gave us open hardware. JAM is giving us an open specification standard for Web3.
It’s platform-neutral, language-agnostic, and built for interoperability at scale. JAM Gray Paper by @gavofyork reflects global, decentralized expertise, with a compute model built for scalable composability.
At @Lollipop_Bulders, we see JAM as the antithesis to proprietary solutions. We see it as a cornerstone of a new digital order. One that breaks down silos and unlocks global interoperability.
In an era of brittle systems and fragile trust, JAM’s openness isn’t just a virtue - it’s a necessity.
To embrace JAM is to embrace a more connected, resilient, and trustworthy digital future.
Why is JAM becoming the new strategic focal point for sovereign nations?
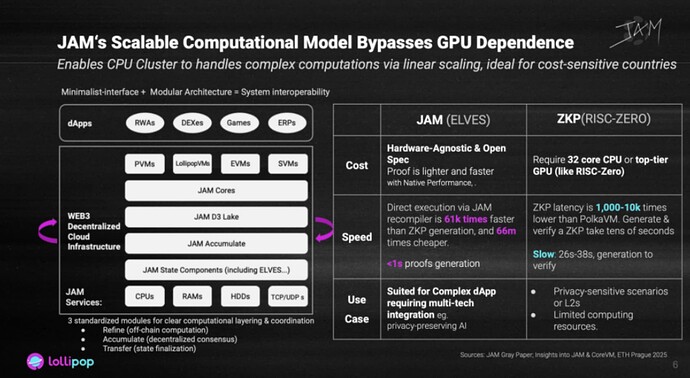
The answer lies in its Scalable Computational Model, a breakthrough enabled by a minimal interface and modular architecture. This model offers exceptional composability, elasticity, and system-level interoperability - exactly what national digital infrastructure needs to remain sovereign and resilient.
At its core, JAM adopts a scale-out architecture that transcends traditional hardware limits. Rather than relying on expensive GPUs for ZK-related computations, JAM enables linear scalability of complex computation across standard CPU clusters. This is a game-changer solution for countries aiming to build resilient compute infrastructure without the high costs or constraints of GPU-based systems.
Its architecture is cleanly decoupled into three standardized functional layers:
- Refinement Layer – Executes off-chain computation
- Aggregation Layer – Coordinates decentralized consensus
- Messaging Layer – Ensures finality and state integrity
Crucially, JAM is built on the RISC-V open specification, meaning it inherits hardware independence and open access to critical compute infrastructure. Its proof system offers cryptographic security comparable to ZKPs (zero-knowledge proofs) but at dramatically lower cost and latency.
According to the JAM Gray Paper, JAM’s proof generation is up to 61,000 times faster than standard ZKPs - with sub-second performance on commodity hardware. ZKPs, in contrast, typically take several seconds and require high-end GPUs.
But JAM doesn’t “optimize ZKP” - it re-architect the way proofs are handled. Through modular compute layers, JAM reallocates energy-intensive steps to the most efficient layer and blends in recursive cryptography. The result is a system optimized for energy-efficiency and hybrid tasks - ideal for privacy-preserving AI and complex multi-module dApps.
Its energy efficiency is now approaching that of Web2 systems, a major milestone in overcoming blockchain’s “energy bottleneck.” For digitally underdeveloped nations, JAM lowers the infrastructure bar and opens a realistic path toward digital sovereignty - even for those previously left on the edge.
JAM’s strategic relevance for sovereign nations is evident. But to fully realize its potential, it requires a robust and future-proof virtual machine layer.
The first widely adopted blockchain VM - EVM - pioneered smart contracts for DeFi, Web3 infrastructure and financial primitives. But its single-threaded execution model imposes fundamental performance ceilings. Even with L2s absorbing transaction volume, true parallelism is never achieved - they merely replicate the same EVM logic in isolated environments and ecosystems.
Solana took a different route with eBPF-based parallelism. While it delivers higher throughput, it’s heavily reliant on high-end hardware and locked into a tightly controlled ecosystem. And At the final stage of processing, transaction execution remains sequential.
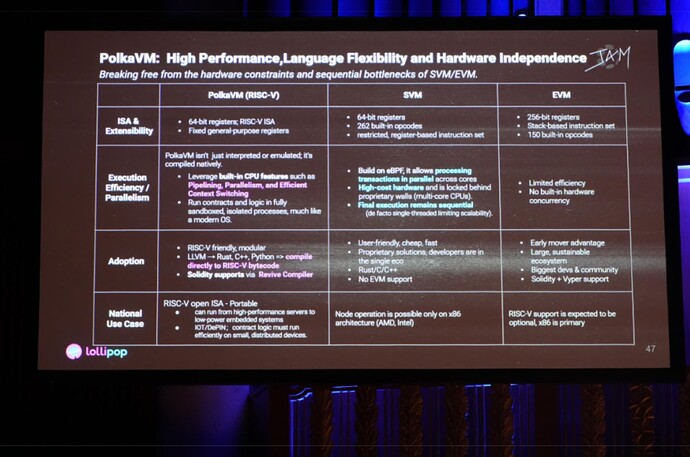
So this is where PolkaVM comes into play, designed from the ground up for Polkadot and JAM, and powered by a RISC-V instruction set architecture that natively supports parallel execution.
PolkaVM delivers three defining advantages:
1. Native Performance
2. Language Flexibility
3. Hardware Independence
First, a performance leap: from interpreted execution to native compilation: PolkaVM abandons the traditional interpreter model used by most virtual machines and instead adopts native compilation. By directly leveraging the CPU’s pipeline processing, parallel execution, and efficient context switching, it delivers execution speeds approaching that of native operating systems. Smart contracts run inside fully isolated sandboxed processes, achieving a security model comparable to modern OS architectures.
Second, language abstraction: breaking the developer lock-in:
Developers are no longer restricted to a single smart contract language. PolkaVM supports various languages such as Rust, C, and Go for contract development, compiling directly into RISC-V bytecode. Through the Revive compiler, it also supports Solidity compatibility, enabling seamless migration of existing EVM-based projects.
Third, hardware-flexible deployment: a truly portable execution layer:
PolkaVM is built on the open RISC-V standard, making it highly portable. It can run smoothly on everything from high-performance servers to low-power embedded devices. This flexibility makes it a perfect fit for use cases like IoT, DePIN, and blockchain-based robotics - where smart contracts need to run efficiently at the edge of the network.
In short, PolkaVM is where the openness of RISC-V, the native parallelism of CPU architecture, and a multi-language development ecosystem converge. It lays a foundational layer for the next generation of decentralized applications - combining performance, flexibility, and openness by design.
Part 3: JAM as the Breakthrough: A Peer-Level Solution to the Digital Sovereignty Dilemma
One of the most persistent challenges in today’s blockchain landscape is the lack of a unified interoperability framework that seamlessly bridges permissioned and permissionless systems.
For sovereign nations navigating this digital terrain, three requirements are particularly critical:
- Compliance Autonomy: Each jurisdiction must retain the ability to define and enforce its own regulatory parameters, independent of external control.
- Open Interoperability: Cross-border integration with permissionless systems must remain intact.
- Cross-Compliance Domains Connectivity: Secure, direct communication between distinct permissioned compliance systems must be not only allowed, but technically straightforward.
This is precisely where JAM introduces a fundamental architectural breakthrough.
For the first time, it enables the systemic integration of all three critical requirements - at the infrastructure layer.
By combining peer-to-peer cross-chain messaging with heterogeneous sharding, the JAM protocol establishes a secure and sovereign collaboration framework tailored to highly customizable environments.
Its core innovation lies in dual compatibility:
- On one side, it enables flexible configurations to meet the specific governance needs of sovereign actors.
- On the other, it preserves the core strengths of permissionless architectures - essential for cross-border interaction of stablecoins and real-world assets (RWA).
This architectural synthesis reconciles two traditionally opposing paradigms: the need for regulatory sovereignty and the openness of decentralized networks—brought together seamlessly at the infrastructure level.
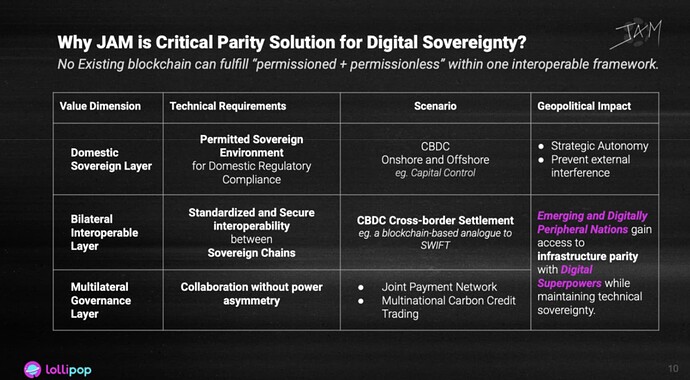
JAM represents the only existing technical architecture capable of delivering full-spectrum digital sovereignty within permissioned, sovereign environments - such as those required for CBDCs.
Its distinguishing value proposition resides in a sophisticated three-layered framework:
1. Domestic Sovereignty Layer: Empowers each nation to deploy sovereign instances tailored to their regulatory needs - forming compliant, fully controlled digital infrastructure. For Emerging and Peripheral Digital Nations, JAM substantially reduces the barriers to access high-security, high-performance sovereign systems.
2. Bilateral Interoperability Layer: Establishes standardized and secure channels between sovereign blockchains - functionally analogous to SWIFT in traditional finance. These channels enable trusted cross-border payments and settlements while preserving equal and secure digital sovereignty for both interacting parties.
3. Multilateral Governance Layer: Leveraging JAM’s global neutrality, this layer introduces a fair participation framework - allowing developing nations to engage in multilateral cooperation on equal footing with digital superpowers. It offers a practical mechanism to reduce power asymmetries and foster consensus-driven, voluntary collaboration.
In this architecture, JAM is inherently aligned with the logic of a multipolar world. It provides the foundational infrastructure for a globally inclusive financial base layer - one where all participants, regardless of economic or technological stature, can access sovereign-grade digital capabilities.
JAM is not just a protocol. It is a structural pillar in the evolution of a fair and interoperable global digital order - and a critical enabler of equitable digital finance in a world defined by pluralism and sovereignty.
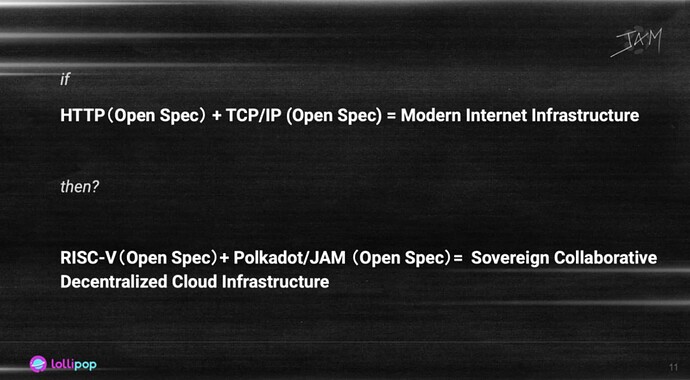
The paradigm shift from hardware-dependent WWW to RISC-V to JAM reflects a clear and continuous evolution in the legacy of open standards - each wave redefining how technological power is distributed.
Tim Berners-Lee laid the foundation for the modern internet by inventing hypertext atop the TCP/IP protocol stack - a milestone in open specification that shaped the foundational architecture of the Web.
RISC-V extended this logic to the hardware domain, breaking the monopoly of proprietary chip design with an open instruction set, ushering in a new era of democratized computing at the processor level.
JAM now defines the next frontier in this lineage: a protocol that defines a decentralized, permissionless, and verifiable compute base for the Web3 era. By leveraging open communication-layer protocols and distributed compute resources, JAM introduces a new trust foundation for sovereign digital systems.
Each of these technological waves - WWW, RISC-V, and JAM - follows a shared logic: open specifications restructure control and powers.
Together, RISC-V and JAM are poised to co-create a new kind of decentralized cloud - sovereign, collaborative, and non-monopolistic. In doing so, these technologies challenge existing models of global infrastructure and offer a viable path toward a more equitable, open digital future.