Token Syndication, Economic Distribution, and Distributed Security in Polkadot
Token Syndication, Economic Distribution, and Distributed Security in Polkadot
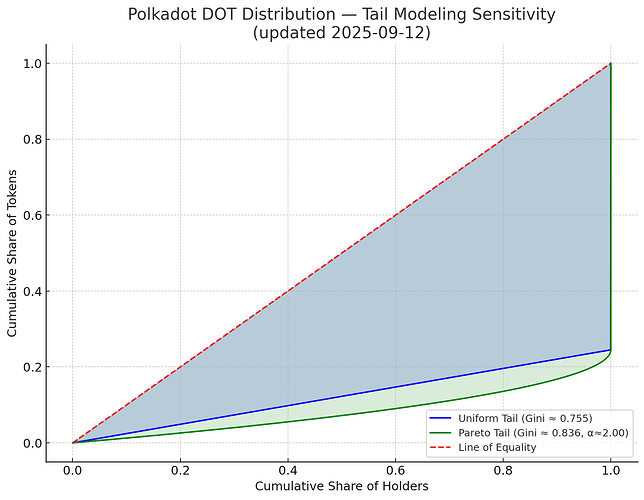
Visual Context: Gini Coefficients for DOT Token Distribution
Recent analyses estimate Polkadot’s token distribution Gini coefficient between 0.75 and 0.84, depending on whether we assume a uniform or power-law tail for small holders.
This Lorenz curve below visualizes the current state:
Blue = uniform tail (Gini ≈ 0.75), Green = Pareto tail (Gini ≈ 0.84). Top 100 holders control ~77.5% of supply.
1. Definitions: From Ownership to Operational Control
Let’s be precise about our terms:
- Token syndication: coordination mechanisms that route concentrated capital (large holders) into many independent operators (validators, collators, service providers) via nomination pools, delegation caps, and custody separation—without requiring redistribution.
- Economic distribution: the cash-flow spread across independent principals. What matters is not who holds tokens, but who earns revenue from protocol services.
- Distributed security: no small coalition can halt, censor, or corrupt the protocol because effective control is dispersed across uncoordinated, incentivized actors.
2. A Necessary Condition: Cost of Corruption vs. Benefit of Attack
Let:
- ( p ) = DOT price (set by market demand)
- ( S ) = total stake bonded
- ( f ) = minimum fraction of control needed to compromise the system
- ( CoC = p ⋅ S ⋅ f ) = Cost of Corruption
- ( BoA ) = Benefit of Attack (e.g., MEV, censorship, governance capture)
On any present-value basis, the system is economically secure if:
CoC > BoA
- Token syndication raises ( f ): requiring a broader coalition to attack.
- Token demand raises ( p ): increasing the cost to acquire control.
Thus, distributed security is not achieved by redistribution alone—it emerges from price × distribution of operational control.
This includes dynamic scenarios such as those discussed in previous comments of mine on threads opened by Web3 Foundation representatives discussing economic security (Polkadot’s Economic Resilience and the Role of Inflation).
3. Why Syndication Requires Economic Distribution
Syndication alone isn’t enough. If most operators are controlled by the same entity, ( f ) remains low.
To truly raise the cost of corruption:
- Delegation caps, custody diversification, and operator independence are essential.
- Cash flow must sustain those operators: decentralization is durable only if it’s economically viable.
- Economic distribution funds opex/capex without subsidies or inflation.
This keeps decentralization from becoming a short-lived grant artifact.
4. Token Demand Enforces Structural Responsibility
DOT demand does more than raise price—it enforces economic discipline:
 1. Price boosts Cost of Corruption ( CoC )
1. Price boosts Cost of Corruption ( CoC )
Higher external demand → higher DOT price → increased ( CoC ).
Attackers must spend more capital to gain control.
 2. Revenue sustains decentralization
2. Revenue sustains decentralization
When protocol services (e.g., coretime, identity, messaging) are priced in DOT:
- Operators earn fees.
- Independence becomes sustainable.
- Treasury dependence shrinks.
 3. Performance matters under demand
3. Performance matters under demand
Syndicated capital flows to the best operators:
- High uptime, reliability, and low latency are rewarded.
- Poor performers lose stake, flow, and relevance.
- Large holders are incentivized to optimize, not idle.
 4. Demand raises the opportunity cost of collusion
4. Demand raises the opportunity cost of collusion
Censoring or coordinating an attack costs the attacker future recurring revenue.
A high-demand protocol punishes bad actors economically.
4.5 Why Pricing Services in Stablecoins Reduces Economic Security
Let k ∈ [0,1] denote the demand-coupling coefficient: the fraction of service value that converts into direct DOT buy pressure (sinks/burns/bonds).
- If services are priced in DOT, k ≈ 1
- If services are priced in stablecoins, k → 0 unless the protocol forces conversion into DOT sinks
Why this weakens security:
-
Demand decoupling → Lower ( p ) and often lower ( S )
Usage growth doesn’t require acquiring DOT. This reduces CoC = p ⋅ S ⋅ f -
Revenue loop breaks
Stablecoin fees bypass DOT buyback paths. Cash flow no longer supports token security. -
Asymmetric attack calculus
If ( BoA ) accrues in stablecoins while ( CoC ) must be paid in DOT, attack costs fall relative to benefits. -
Operator centralization pressure
When revenues are in stablecoins but slashing risk is in DOT, smaller operators face hedging volatility and get priced out.
Mitigations (if UX requires stablecoins):
- On-chain auto-conversion (AMM or vaults) to enforce DOT sinks . This includes my asynchronous Pareto-optimal convex optimized algorithm, but applied in this case for token exchange ( See RFC-0152: Decentralized Convex-Preference Coretime Market for Polkadot to check the setup needed for this application, with Agile Coretime as a market example and the original Paper in progress describing the algorithm construction)
- Service access bonds in DOT (collateralized metering)
- Fee burning or staking denominated in DOT
5. Design Rules (No Redistribution Required)
 Price services in DOT: Coretime, messaging, identity, data availability
Price services in DOT: Coretime, messaging, identity, data availability Syndicate with exposure caps: Encourage pool diversity and custody separation
Syndicate with exposure caps: Encourage pool diversity and custody separation Pay-for-performance: Cash flows should reflect real operational value measured in service revenue
Pay-for-performance: Cash flows should reflect real operational value measured in service revenue Detect control correlation: Track and make transparent clusters among operators and entities
Detect control correlation: Track and make transparent clusters among operators and entities Fund Treasury with KPI-bound proposals: Only back builders with DOT-denominated usage goals
Fund Treasury with KPI-bound proposals: Only back builders with DOT-denominated usage goals If stables are used at UX, enforce DOT sinks: Auto-convert or settle in DOT to keep ( k ) high
If stables are used at UX, enforce DOT sinks: Auto-convert or settle in DOT to keep ( k ) high
6. Metrics That Prove It
- Effective Nakamoto coefficient (by ultimate control, not just validator count)
- HHI or Gini of cash flows: Who earns, not who owns
- Syndication Coverage Ratio: % of stake delegated across independent operators
- Demand KPIs: DOT fees per block, coretime revenues, DOT auto-converted from stables
- Security margin: Proxy of ( CoC ) / ( BoA ) using slashing risk and market depth
 TL;DR
TL;DR
- Token syndication increases ( f ), the number of actors required to attack
- Token demand increases ( p ), making DOT expensive to acquire
- Stablecoin-based service pricing decouples demand from DOT, reducing ( CoC ) unless converted into DOT sinks
- Protocol security emerges when DOT is a priced asset, not just a staked one
Authored by Diego Correa T.
CTIO at Ikkuna SpA · Founder | OnEdge Network
LinkedIn · GitHub