I take the opportunity of the post being reopen to share my discussion on Discord with @frankywild .
We keep on discussing after the initial post was closed in the Polkadot forum, Franky contacting me directly in a proactive manner.
Because yes, you can have a civil discussion with people.
And yes, you can agree to disagree without reaching any super level of toxicity, as it is currently on most open threads about governance topics.
So, as a summary, I’m fine with the answers and explanations i was given:
1/ X Badge
X badge is NOT the blue/yellow tick you can find on X accounts.
It is paid because they have people from different continents using the account, and when they didn’t have that badge, X was everytime asking for verifications and making lot of trouble for them, with that badge, X don’t ask anymore.
It’s a $166/month cost.
We can disagree about the content scope being included in the anti-scam bounty, but it’s clear on my side now. 
X management account = 800$/month, not 3250$ as i thought initially.
2/ Scope of the scams being taking down
As per the list of websites available on polkadot.js, it can be confusing to find sites with names without any relation with the ecosystem, but that doesn’t mean the ecosystem is not targeted.
Franky provided me sone example as shown below:
-
some of those sites are fake crypto exchanges where you can send your DOT and receive nothing in change
-
In Github repo there are many sites that even if you enter them, you can’t see any target from our ecosystem, those are not rewarded
As a constructive feedback, i told that the bounty should showcase how they operate and what they are taking down. Just a few examples from time to time can help to have a better understanding.
It’s a global feedback for all bounties: just showcase what you are doing. Reports are necessary, but they are “cold reports”.
3/ Report improvements
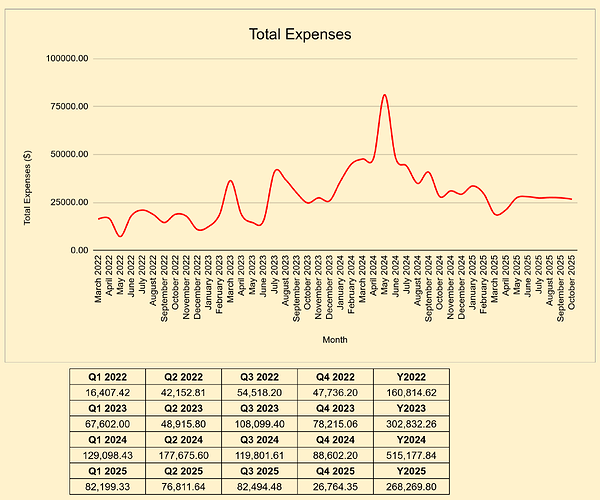
Most of misunderstandings, not only on my side but also on the community side, come from the report itself.
I provided my feedbacks to Francky to improve the report, distinguinshing “Payments” and “rewards” on one hand, and indicating the frequency on the other hand (One time payment, monthly, quarterly, annually).
It should help the readability and avoid misunderstandings. Because we all do the same mistake:
- Take a given month
- Sum the “rewards” per person
- Ask questions about anomalies (or what we think to be anomalies).
The mix between “payments” (cash out) and “rewards” (cash in) for a given person is by design wrong.
Conclusion
I let Franky add any additional details if needed but i’m happy we had a normal discussion between 2 people.
I hope the forum will stay a place of exchange, before being a place of finger pointing. We all have a responsability to maintain a good place to build.
Cheers.