@AlinaZ Let’s stop sugarcoating things.
You claim to be “fully aware” of the tool you’re using, yet everything you’ve said so far suggests a severe lack of practical experience.
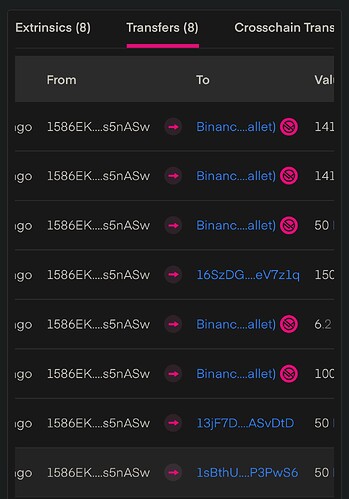
Anyone with a minimum of on-chain literacy knows exactly how Binance and Kraken handle deposit addresses. These platforms generate user-specific hot wallets and they’ve done so for years. Why? To simplify attribution and automate crediting systems internally. Also partly for traceability ![]() . This is not up for debate it’s standard CEX infrastructure.
. This is not up for debate it’s standard CEX infrastructure.
So when you say you’re not sure if an address is user-specific despite Merkle Science (your own provider!) and Subscan both labeling it clearly it just looks like you’re grasping at straws to defend a weak position.
And no, this isn’t about waiting days to “identify the swap service.”
It’s about understanding the mechanics of how CEX deposit flows actually work something you should already know if you’re in charge of tracking stolen funds.
Let’s be honest: Merkle Science is the tool your team pays for. So trying to discredit its output now that someone else is using it more effectively? That’s amateur hour.
If you’re serious about improving anti-scam response, you need to step up your game because right now, what you’re demonstrating is not just disappointing, it’s counterproductive.
Enough with the vague disclaimers. Be precise. Be competent. Or let someone else take over.
— Cyphertux ![]()